DIAS Hack-A-Truck: Part 1
2 days, 5 teams, 1 question: Can you deactivate the environmental protection system of a truck?
During the first DIAS hackathon, participants came up with creative technical ideas to find attack vectors which can be exploited to make tampering business out of them.
The Hack-a-Truck was held on the 19th and 21st of May.

The problem
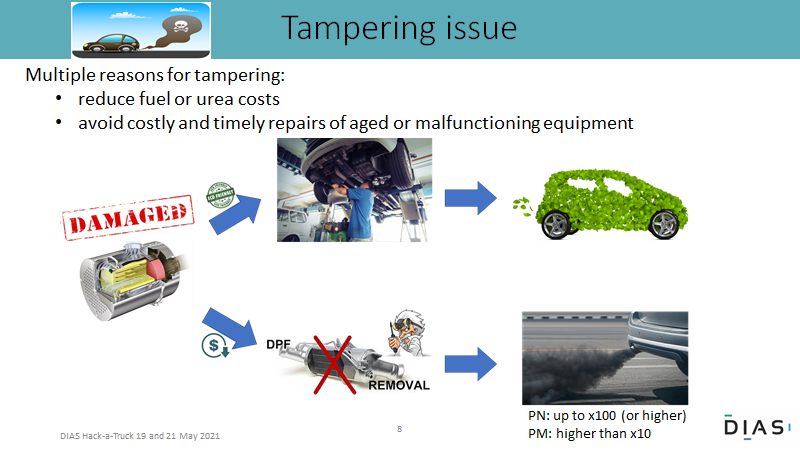
Malicious tampering of environmental protection systems turns very clean vehicles in heavy polluters. In the European project DIAS, countermeasures are developed to harden vehicles against malicious tampering and this needs to be thoroughly tested. Creative, ingenious people were invited to hunt for attack vectors. A hackathon was organized where 5 teams containing people with various skills worked out a virtual plan, from finding an attack vector (to deactivate or remove an environmental protection systems) to making business out of it.
Hackathon = hacking + marathon
-
5 teams to battle for the best tampering plan
-
3 technical trainings + Q&A
-
2 brainstorm sessions to collect all possible attack vectors and select the most promising one(s)
Hack-a-Truck was an online automotive hackathon which lasted two days in total. To get the participants up to speed, three trainings were hosted by experts from industry-leading companies and knowledge institutes, such as Ford Otosan, Bosch and TNO. The participants were informed by the experts about the latest and the greatest new environmental protection systems, ECU and communication systems, tampering methods and the newly developed state-of-the-art countermeasures by DIAS consortium. In between these trainings, the participants were assigned to a group of people with complementary skills and worked together on finding attack vectors in a defined truck set-up. Together, they worked out a business plan as if they were to commercialize the tampering product on the EU market.

Schedule
-
Trainings: Technical trainings and an introduction to the problem to get participants up to speed
-
Working sessions: The action happened in a sequence of working sessions where participants brainstormed to find attack vectors. Then the teams worked out the most promising attack vectors from the brainstorm in a technical plan and a business plan. During the working sessions a pool of experts was readily available to provide any information and give a first feedback whether the proposed attacks will work or not.
-
Presentation of the plan: Each team made a presentation composed of the technical plan and the business plan based on the template that was used for the brainstorm and during the working sessions.
-
Jury deliberation and awards: The jury ranked the tampering plans based on the technical plan and the simple business plan. DIAS aims to make tampering tough and expensive (prevention) and aims to detect tampering. Therefore, the most important criteria for judging the plans were related to complexity/robustness, price, and risk of detection.
Profile of participants
The participants had an interest in and experience with exhaust gas aftertreatment systems, (automotive) electronics and (automotive) communication and security protocols.
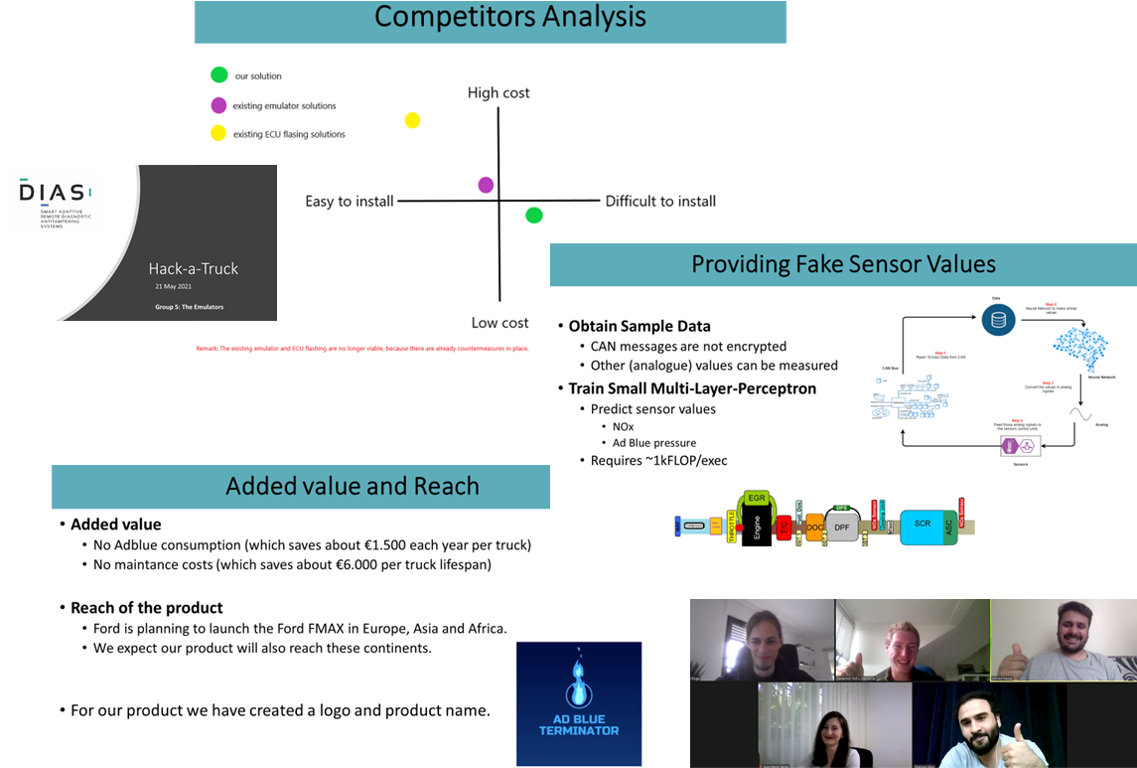
The winners
"The Emulators" team might not have selected the most groundbreaking name, but their plan was well thought over and they convinced the jury of the first DIAS hackathon.
More information can be found in a DIAS public report which will be available soon.